Here are some features Check Point 600 appliance has:
1. Get access your appliance from anywhere
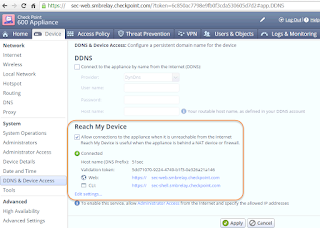
This feature is quite useful to the users who is behind the firewall or proxy and have limited access to Internet. You can register your device with Check Point smbrelay domain to get a unique web and cli log in link. It can bypass your client side firewalls and proxy settings since it is using https protocol. Do not forget to enable Internet access to your appliance. By default, your 600 appliance will deny all Internet access to itself for security reason.This service is provided by Check Point’s Reach My Device service. Two links will be displayed under Reach My Device section:
- https://xxx-web.smbrelay.checkpoint.com - for Web Admin GUI
- https://xxx-shell.smbrelay.checkpoint.com - for SSH Admin CLI
To allow the access to your device from Internet:
- Register your device from the "DDNS & Device Access" screen;
- Make sure your IP address (194.108.184.63) is permitted from the "Administrator Access" screen.
Check Point 600 Appliance also provides SSH access to device itself.
pi@raspberrypi:~$ ssh -l admin 192.168.2.1
admin@192.168.2.1's password: Gateway-ID-640> fetch - Fetch operation set - Set operation fw - VPN-1/FireWall-1 commands cpwd_admin - cpwd_admin commands show - Display operation upgrade - Upgrade the software image of the system revert - Revert the system to the previous software image or to factory-defaults backup - Create a backup file restore - Restore previous system settings test - Test operation shell - Switch to expert mode resize - Set terminal settings to current window size expert - Switch to expert mode cpshell - Start cpshell cpstart - Start Firewall services cpstop - Stop Firewall services cphaprob - Defines critical process of High Availability cphastart - Enables High Availability on the appliance cphastop - Disables High Availability on the appliance cpstat - Display Check Point statistics info ping - Ping traceroute - Traceroute arp - arp top - Provide a view of process activity in real time uptime - Display the time since the last boot netstat - Display networking information sim - SecureXL Implementation Module commands vpn - Control VPN dynamic_objects - Configure/Display dynamic objects reboot - Use to reboot the system ver - Show Check Point firewall version tcpdump - Packet analyzer nslookup - Name server lookup cpinfo - Check Point Support Information sleep - Sleep, pause for a time equal to the total of the args given exit - Exit from shell add - Add operation delete - Delete operation send - Set operation find - Display operation connect - Set operation update - Set operation reconnect - Set operation Gateway-ID-640> Gateway-ID-640> show configuration # Configure a persistent domain name for the device set dynamic-dns provider "DynDns" # Configure DNS and Domain settings for the device set dns proxy "enable" resolving "on" set dns mode "internet" # HTTPS categorization ....... <Outputs Omitted> |
2. Guest Wireless Network with Hotspot
This feature will add extra virtual access point for your guests. You can use customized web portal to grant user access based on user groups you created on local database or Active directory database.3. Enterprise Level Security Features
You will get all following enterprise level features if you have license. Some of them you wont be able to see in other vendor's similar level products:- Firewall
- Application Control & UTL Filtering
- User Awareness
- QoS
- Intrusion Prevention
- Anti-Virus
- Anti-Spam
- Remote Access
- Site-to-Site VPN
 |
| Security Dashboard |
During the testing, I have enabled Firewall, Applications & URL Filtering, IPS, Anti-Virus and Anti-Bot those five bladed to check how effective they are.
4. Easy to Set up Policy for Access, Threat Prevention and VPN
Check Point 600 appliance provides pre-defined policy for you to select. For example, for firewall access policy, you can easily choose between Strict and Standard for your needs. You do not have to go to deep to define your own policy one by one. There are switches to let you choose on or off for each blade. |
| Access Policy |
 |
| Threat Prevention |
 |
| VPN |
5. User Awareness Support Active Directory or Browser Based Authentication
The user awareness blade links usernames to machines, allowing security policies to be applied to user identities. Support for remote workers is excellent: they can connect using Check Point's mobile desktop client, a remote app for iOS and Android, SSL VPNs and L2TP. |
| User Awareness |
6. Rich Reporting and Monitoring functions
The appliance can generate hourly, daily, weekly and monthly reports showing all network activity, top web categories, security threats and intrusion alerts. Each report also provides a bandwidth analysis and descriptions of events and application types but you can only print and not export them. |
| Monitering |
 |
| Reports |






No comments:
Post a Comment