VPN Lab Series:
Cisco VPN LAB 1 : Simple Easy VPN Example between Routers and Comparison with DMVPN
Cisco VPN LAB 2 : IPSec VPN Example Between Two ASA 8.4.2
Cisco VPN LAB 3 : EZ VPN Between ASA 8.4.2, IOS Router and EZVPN Client Software
Working on Easy VPN and DMVPN, I completed this first lab for EZVPN lab and also list some using resource at the bottom of this post.
Cisco VPN LAB 1 : Simple Easy VPN Example between Routers and Comparison with DMVPN
Cisco VPN LAB 2 : IPSec VPN Example Between Two ASA 8.4.2
Cisco VPN LAB 3 : EZ VPN Between ASA 8.4.2, IOS Router and EZVPN Client Software
Working on Easy VPN and DMVPN, I completed this first lab for EZVPN lab and also list some using resource at the bottom of this post.
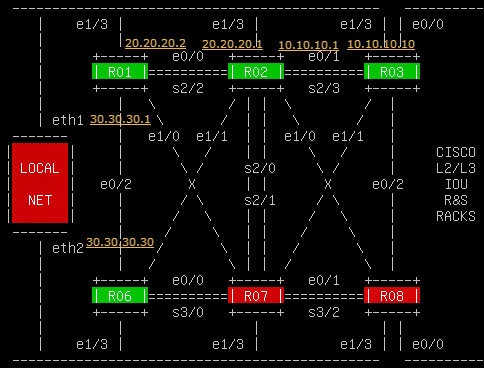
1. Topology
It is still with my favorite IOU rack v3. The physical connection with IP addresses have been shown on the diagram.
2. Configuration: (Redundancy configuration have been omitted)
@EZVPN Server Configuration
R1#show run
Building configuration...
Current configuration : 2631 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
security passwords min-length 1
!--- Enable Authentication, Authorizing and Accounting (AAA)
!--- for user authentication and group authorization.
aaa new-model!--- Enable the AAA commands in order
!--- to enable Xauth for user authentication.
aaa authorization network hw-client-groupname local !--- Enable the AAA commands
!--- in order to enable group authorization.
aaa authorization network groupauthor local !
!
!
!
aaa session-id common
clock timezone CST 8
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip source-route
!
ip cef
no ip domain lookup
no ipv6 traffic interface-statistics
no ipv6 cef
!
multilink bundle-name authenticated
!--- Define the username and password to use for Xauth.
username cisco password 0 cisco123!
redundancy
!
!--- Create an Internet Security Association and
!--- Key Management Protocol (ISAKMP) policy for Phase 1 negotiations.
crypto isakmp policy 1authentication pre-share
group 2
crypto isakmp client configuration address-pool local dynpool
!
!--- Create a group with the pre-shared key for IKE authentication.
crypto isakmp client configuration group hw-client-groupnamekey hw-client-password
!--- Create the Phase 2 policy for actual data encryption.
crypto ipsec transform-set transform-1 esp-des esp-sha-hmac !
!--- Create a dynamic map and
!--- apply the transform set that was created earlier.
crypto dynamic-map dynmap 1set transform-set transform-1
reverse-route
!
!--- Create the actual crypto map,
!--- and apply the AAA lists that were created earlier.
!--- These commands associate the AAA commands to the crypto map.
crypto map dynmap isakmp authorization list hw-client-groupnamecrypto map dynmap client configuration address respond
crypto map dynmap 1 ipsec-isakmp dynamic dynmap
!
!--- Apply the crypto map on the interface where
!--- traffic leaves the router.
interface Ethernet0/0description connected to Internet
ip address 20.20.20.2 255.255.255.0
crypto map dynmap
!
interface Ethernet0/1
no ip address
shutdown
!
interface Ethernet0/2
ip address 30.30.30.1 255.255.255.0
!
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 Ethernet0/0
!
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
!
exception data-corruption buffer truncate
end
@EZVPN Client Configuration
R2#sh run
Building configuration...
Current configuration : 2420 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
security passwords min-length 1
!
aaa new-model
!
!
aaa authentication login userauthen local
aaa authorization network groupauthor local
!
aaa session-id common
clock timezone CST 8
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip source-route
!
!
ip cef
no ip domain lookup
ip domain name cisco.com
no ipv6 traffic interface-statistics
no ipv6 cef
!
multilink bundle-name authenticated
!
username cisco password 0 cisco123
!
redundancy
!--- Set the parameters to connect to the
!--- appropriate Easy VPN group on the Easy VPN server.
crypto ipsec client ezvpn hw-clientconnect auto
group hw-client-groupname key hw-client-password
mode client
peer 20.20.20.2
xauth userid mode interactive
!
!--- Use the crypto ipsec client ezvpn <name> command on the
!--- interface that connects to the Easy VPN server
!--- in order to complete the Easy VPN.
description INTERNET
ip address 20.20.20.1 255.255.255.0
crypto ipsec client ezvpn hw-client
!--- Define the inside interfaces that will access
!--- and can be accessed via Easy VPN.
interface Ethernet0/1description LAN
ip address 10.10.10.1 255.255.255.0
crypto ipsec client ezvpn hw-client inside
!
interface Ethernet0/2
no ip address
shutdown
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 Ethernet0/0
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
!
exception data-corruption buffer truncate
end
3. Verify
R2#show crypto ipsec sainterface: Ethernet0/0
Crypto map tag: Ethernet0/0-head-0, local addr 20.20.20.1
protected vrf: (none)
local ident (addr/mask/prot/port): (30.30.30.20/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 20.20.20.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 20.20.20.1, remote crypto endpt.: 20.20.20.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x2B595786(727275398)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xD56D693B(3580717371)
R2#show crypto ipsec client ezvpn
Easy VPN Remote Phase: 8
Tunnel name : hw-client
Inside interface list: Ethernet0/1
Outside interface: Ethernet0/0
Current State: IPSEC_ACTIVE
Last Event: MTU_CHANGED
Address: 30.30.30.20 (applied on Loopback10000)
Mask: 255.255.255.255
DNS Primary: 30.30.30.10
DNS Secondary: 30.30.30.11
NBMS/WINS Primary: 30.30.30.12
NBMS/WINS Secondary: 30.30.30.13
Default Domain: cisco.com
Save Password: Disallowed
Current EzVPN Peer: 20.20.20.2
When ping from R2 (10.10.10.1) to R6 (30.30.30.30) and show crypto ipsec sa, we see encrypted packet is 5 but decrypted packet is 4. That is because first ping packet failed to reach the destination as we can see it from ping following result. After that, all ping packets will be encrypted and decrypted properly.
R2#ping 30.30.30.30 source 10.10.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.30.30.30, timeout is 2 seconds:
Packet sent with a source address of 10.10.10.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 4/5/8 ms
R2#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: Ethernet0/0-head-0, local addr 20.20.20.1
protected vrf: (none)
local ident (addr/mask/prot/port): (30.30.30.20/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 20.20.20.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
******Some Other Resources.
From Cisco page:
- Cisco Enhanced Easy VPN and DMVPN Comparison
- Cisco Site-to-Site VPN Solution Comparison






No comments:
Post a Comment