1. Using Syslog
On Check Point management station, you can follow these steps to redirect firewall logs and audit logs to the external syslog server:a) Vi /etc/syslog.conf, on the management station, and add the following line at the end of the file:
local5.info @hostnamesuch as :
local5.info @10.94.20.23
where ‘10.94.20.23’ is the IP of the syslog server (Juniper STRM).
b) if your management server is SecurePlatform - Execute ‘service syslog restart’.
c) Add this command to /etc/rc.d/init.d/cpboot:
fw log -ftnl | logger -p local5.info -t Firewall &
or
forward audit log to external syslog server by add following command:
fw log -ftnl $FWDIR/fw.adtlog | awk 'NF' | logger -p local5.info -t Firewall_Audit &
d) reboot Checkpoint management server and configure a new log source in STRM. Deploy Changes to STRM as well.
e) Verify:
tcpdump host 10.94.20.23[Expert@CP-Mgmt]# tcpdump host 10.94.20.23
tcpdump: listening on Mgmt
12:54:18.534293 CP-Management.syslog > 10.94.20.23.syslog: udp 253 (DF)
12:54:18.538859 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:18.539622 CP-Management.syslog > 10.94.20.23.syslog: udp 225 (DF)
12:54:18.540382 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:18.541115 CP-Management.syslog > 10.94.20.23.syslog: udp 252 (DF)
12:54:18.541904 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:20.536629 CP-Management.syslog > 10.94.20.23.syslog: udp 280 (DF)
12:54:20.538424 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:20.539194 CP-Management.syslog > 10.94.20.23.syslog: udp 228 (DF)
12:54:20.540009 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:22.539075 CP-Management.syslog > 10.94.20.23.syslog: udp 225 (DF)
12:54:22.543184 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:28.540703 CP-Management.syslog > 10.94.20.23.syslog: udp 249 (DF)
12:54:28.543712 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
12:54:28.544410 CP-Management.syslog > 10.94.20.23.syslog: udp 225 (DF)
12:54:28.545036 CP-Management.syslog > 10.94.20.23.syslog: udp 16 (DF)
On STRM server 10.94.20.23, you should be able to see following logs activities:
2. Using OPSEC / LEA
a. Creating an OPSEC Application Object from Servers and OPSEC tab:
In my lab, STRM_10.94.200.23 created.
b. Write Down and Copy Two SIC DN info for STRM configuration
One is from new created OPSEC application: STRM_10.94.200.23CN=STRM_10.94.200.23,O=CP-Management..wtx8w4
Another is from Mgmt Server CP_Management as show below:
cn=cp_mgmt,o=CP-Management..wtx8w4
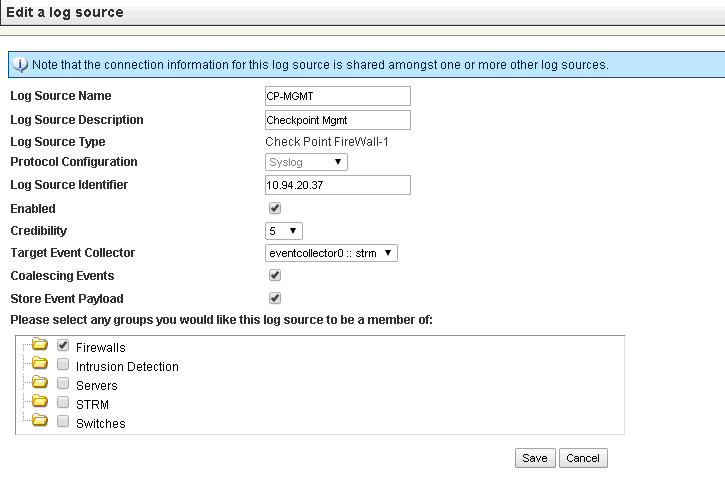
c. STRM Log Source
d. add a new Checkpoint Firewall-1 OPSEC / LEA log Source
e. Verify SIC Connection from Checkpoint Mgmt Server OPSEC Application STRM_10.94.200.23
Reference:
1. Juniper STRM Configuring DSMs2. How to send FireWall logs from Gaia-based Security Management Server to an external Syslog server
3. Forward Logs from Checkpoint SmartCenter Management Server and Juniper NSM / IDP to Syslog Server














No comments:
Post a Comment