Here iss part 2. It will show how to set up the authentication with certifications rather than local UAC users, and get to know the steps how to let SRX and UAC work together to allow the resources to be accessed by users. More related posts list in the following links in this blog:
- Juniper UAC Appliance IC4500 Step by Step Configuration (Part 2) - Certificates based Authentication
- Pulse Secure (formerly Juniper Pulse) - UAC Configuration Summary
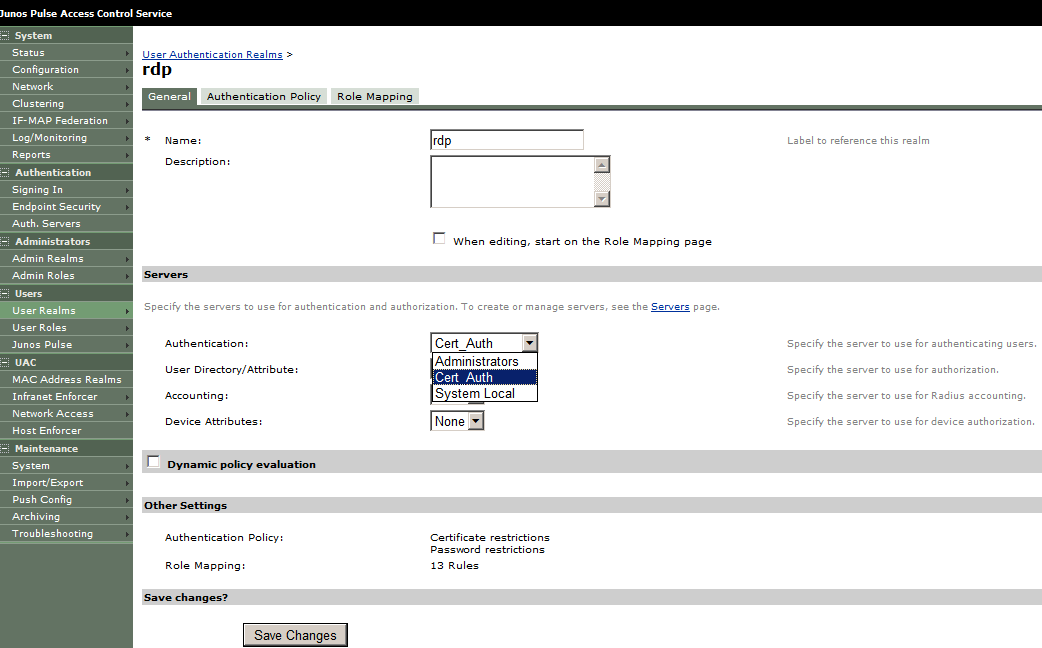
1. Change Authentication mode from System Local to Cert Auth
2. Add users Role Mapping with their Certs
3. Create New Resource Access Policies:
Note: Those policies will match SRX firewall's firewall policy rules.
4. Configure UAC Service on Juniper SRX
services {unified-access-control {
infranet-controller ic4500 {
address 10.9.2.14;
interface reth4.204;
password "$9$f5F/CA0hSeO1eWx7sYn/9A1R"; ## SECRET-DATA
}
inactive: test-only-mode;
traceoptions {
file uac-trace size 2m world-readable;
flag all;
}
}
}
Note:
- UAC device IP address is 10.9.2.14.
- test-only-mode can be enabled for testing purpose
5. Configure SRX Firewall Policy Rule to Use UAC Service
from-zone UNTrusted to-zone Trusted {policy 41 {
match {
source-address n-10.0.0.0;
destination-address h_10.4.2.18_FE_TS;
application [ RDP junos-icmp-ping ];
}
then {
permit {
application-services {
uac-policy;
}
}
}
}
6. Verify
root@fw-uac1> show services unified-access-control status--------------------------------------------------------------------------
Host Address Port Interface State
ic4500 10.9.2.14 11123 reth4.204 connected
root@fw-uac1> show services unified-access-control roles
--------------------------------------------------------------------------
Name Identifier
Users 000000001.000005.0
rdp-role 133882602.503985.0
Total: 2
root@fw-uac1> show services unified-access-control policies
--------------------------------------------------------------------------
Id Resource Action Apply Role identifier
1 tcp://10.4.2.18:3389 allow selected 133882602.503985.0
2 tcp://10.4.2.16:3389 allow selected 000000001.000005.0
Total: 2
root@fw-uac1> show services unified-access-control authentication-table
--------------------------------------------------------------------------
Id Source IP Username Age Role identifier
14 10.9.1.11 John 0 133882602.503985.0
Total: 1
root@fw-uac1> show services unified-access-control counters
--------------------------------------------------------------------------
PIC: cluster1.node0
Sessions allowed
Policy action: 178
Timeout action: 0
Sessions denied
Unauthenticated: 43949
Policy action: 0
Policy not matched: 184
Timeout action: 0
Sessions terminated
Reevaluation: 0
Signout: 13
PIC: cluster1.node1
Sessions allowed
Policy action: 548
Timeout action: 0
Sessions denied
Unauthenticated: 94
Policy action: 0
Policy not matched: 3
Timeout action: 0
Sessions terminated
Reevaluation: 0
Signout: 43











No comments:
Post a Comment