Recently, during an Qualys external Scanning, there is a couple of Vulnerability found which is relate to Plaintext Management Interface. That is because of Telnet port 2002, 9002 is opened on Internet.
It was mentioned before in my previous post. This post just adds more information regarding vulnerability details and how those external scanning tools are responding this vulnerability.
Issues:
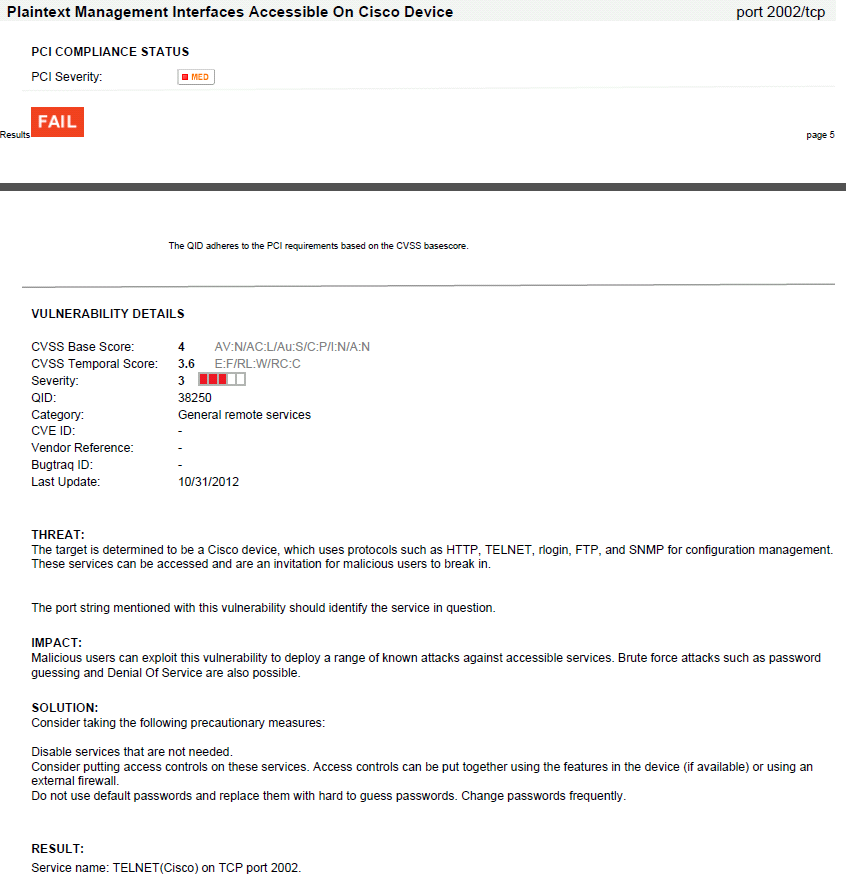
In Qualys PCI Scanning report, it lists this vulnerability detail as following:
Plaintext Management Interfaces Accessible On Cisco Device port 2002/tcp
PCI COMPLIANCE STATUS
PCI Severity: MED
FAIL
VULNERABILITY DETAILS
CVSS Base Score: 4 AV:N/AC:L/Au:S/C:P/I:N/A:N
CVSS Temporal Score: 3.6 E:F/RL:W/RC:C
Severity: 3
QID: 38250
Category: General remote services
CVE ID: -
Vendor Reference: -
Bugtraq ID: -
Last Update: 10/31/2012
THREAT:
The target is determined to be a Cisco device, which uses protocols such as HTTP, TELNET, rlogin, FTP, and SNMP for configuration management.
These services can be accessed and are an invitation for malicious users to break in.
The port string mentioned with this vulnerability should identify the service in question.
IMPACT:
Malicious users can exploit this vulnerability to deploy a range of known attacks against accessible services. Brute force attacks such as password
guessing and Denial Of Service are also possible.
SOLUTION:
Consider taking the following precautionary measures:
Disable services that are not needed.
Consider putting access controls on these services. Access controls can be put together using the features in the device (if available) or using an
external firewall.
Do not use default passwords and replace them with hard to guess passwords. Change passwords frequently.
RESULT:
Service name: TELNET(Cisco) on TCP port 2002.
Plaintext Management Interfaces Accessible On Cisco Device port 9002/tcp
PCI COMPLIANCE STATUS
PCI Severity: MED
FAIL
VULNERABILITY DETAILS
CVSS Base Score: 4 AV:N/AC:L/Au:S/C:P/I:N/A:N
CVSS Temporal Score: 3.6 E:F/RL:W/RC:C
Severity: 3
QID: 38250
Category: General remote services
CVE ID: -
Vendor Reference: -
Bugtraq ID: -
Last Update: 10/31/2012
THREAT:
The target is determined to be a Cisco device, which uses protocols such as HTTP, TELNET, rlogin, FTP, and SNMP for configuration management.
These services can be accessed and are an invitation for malicious users to break in.
The port string mentioned with this vulnerability should identify the service in question.
IMPACT:
Malicious users can exploit this vulnerability to deploy a range of known attacks against accessible services. Brute force attacks such as password
guessing and Denial Of Service are also possible.
SOLUTION:
Consider taking the following precautionary measures:
Disable services that are not needed.
Consider putting access controls on these services. Access controls can be put together using the features in the device (if available) or using an
external firewall.
Do not use default passwords and replace them with hard to guess passwords. Change passwords frequently.
RESULT:
Service name: TELNET(Cisco) on TCP port 9002.
Screenshots:
Active internet connections (servers and established)
Prot Local Address Foreign Address Service State
tcp *:22 *:0 SSH-Server LISTEN
tcp *:23 *:0 Telnet LISTEN
tcp *:2002 88.198.46.51:58719 TCP Protocols ESTABLIS
udp *:123 *:0 NTP LISTEN
udp *:4500 *:0 ISAKMP LISTEN
udp *:161 *:0 IP SNMP LISTEN
udp *:162 *:0 IP SNMP LISTEN
udp *:1975 *:0 IPC LISTEN
udp *:57430 *:0 IP SNMP LISTEN
udp *:500 *:0 ISAKMP LISTEN
Root Cause:
Based on my search, it looks like the Line 2 is used to communicate between the routers and Embedded Service Engine on the Cisco ISR G2 routers.
The article from itcertnotes provides some solutions.
- Complete disable line 2 access
- put an access list on the Line 2 for IPv4 and IPv6.
Solution:
Since Embedded Service Engine is not used that much, there is no need to configure an IP address and put a access-list to restrict access. The simplest solution is to complete disable the access to line 2.
line 2
transport input none








No comments:
Post a Comment