- Set Up IPSec Site to Site VPN Between Fortigate 60D (1) - Route-Based VPNs
- Set Up IPSec Site to Site VPN Between Fortigate 60D (2) - Policy-Based VPNs
- Set Up IPSec Site to Site VPN Between Fortigate 60D (3) - Concentrator and Troubleshooting
- Set Up IPSec Site to Site VPN Between Fortigate 60D (4) - SSL VPN
FortiOS supports the SSL (not SSL1.0) and TLS (TLS1.3) versions defined below:
| Defined | |
|---|---|
| Protocol | Year |
| SSL 1.0 | n/a |
| SSL 2.0 | 1995 - RFC 6176 |
| SSL 3.0 | 1996 - RFC 6101 |
| TLS 1.0 | 1999 - RFC 2246 |
| TLS 1.1 | 2006 - RFC 4346 |
| TLS 1.2 | 2008 - RFC 5246 |
| TLS 1.3 | TBD |
When a remote client connects to the FortiGate unit, the FortiGate unit authenticates the user based on username, password, and authentication domain. A successful login determines the access rights of remote users according to user group. The user group settings specify whether the connection will operate in web-only mode or tunnel mode. There are three types of mode:
- Web-only Mode
- Tunnel Mode
- Port Forwarding Mode (Proxy Mode)
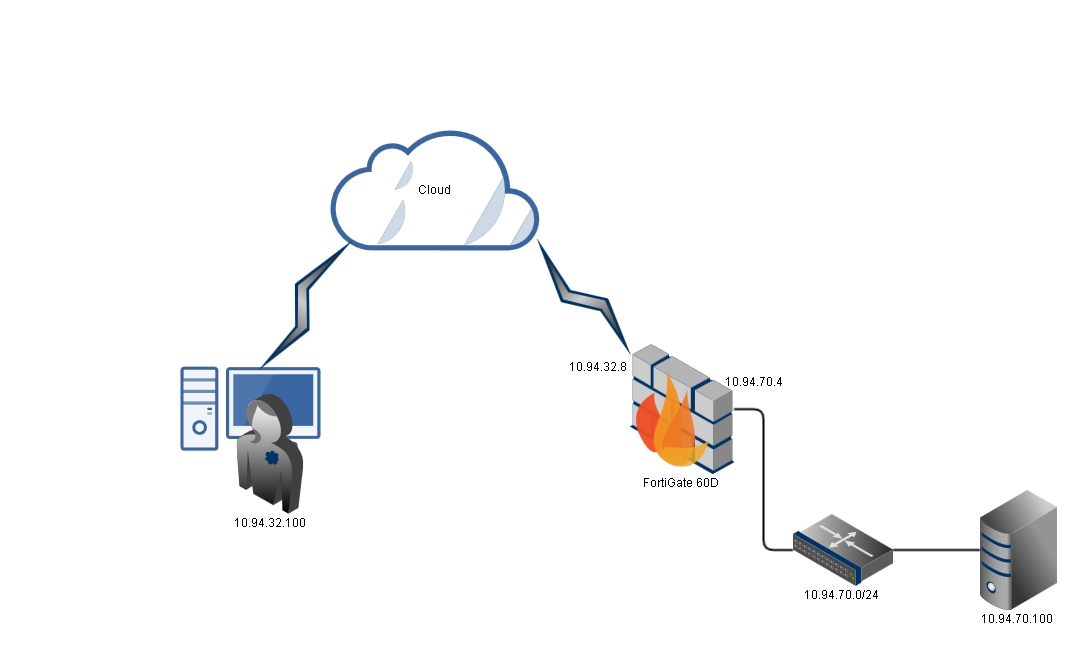
Lab Topology:
Configuration Steps:
1. Create SSL VPN Portal
2. Create Remote Users and Groups
3. Create Security Policies
3.1 SSL-VPN Rule from WAN1 to Internal
3.2 Firewall Address Policy from SSL Tunnel Address to Internal
4. Test
Reference:
- FortiOS™ Handbook - SSL VPN (VERSION 5.2.2)
- How to setup SSL VPN (Web & Tunnel mode) for remote access
- Chapter 16 SSL VPN for FortiOS 5.0
- Setup examples : Remote Access with SSLVPN













No comments:
Post a Comment