- TekRADIUS Usage for AD Authentication
- Cisco Switch Radius Configuration Work With TekRADIUS AD Authentication
- Troubleshooting Cisco Radius Configuration with Free Radius Server TekRadius
Those configuration have been proven working well with Checkpoint, Juniper and Cisco devices. Recently our Juniper NSM upgraded to Juniper Space platform. There were some challenges to set up TekRADIUS to work with JunOS Space during configuration. Here are all steps I did and so far it works.
1. Download and Install TekRADIUS
You can get installation file from download page. Current version is 4.9.9. You can use LT version which is SQLite version. Installation is quite straightforward, and configuration is simple as well.
2.TekRADIUS configuration.
TekRADIUS configuration is able to be done from console window. Go through all tab interfaces and put necessary information in. Your Radius server should be able ready in 10 minutes. In my lab configuration, there are some groups defined in TekRADIUS group tab. Admin group is using active directory authentication and it will automatically log into cisco devices enable mode with privilege 15. All admiistrators defined in users tab will be nested in those groups.
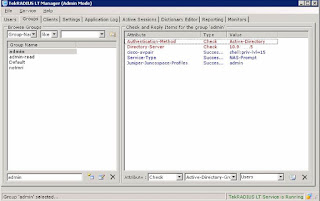 |
| Defined Groups |
For the users in admin-read group, difference from admin group is not able to log into enable mode automatically. You will have to enter enable password manually from Cisco device. In admin-read group, there are no cisco-avpair attribute in Success-reply packets.
 |
| Radius Client Configuration |
 |
| Radius Server Configuration |
 |
| Cisco Attribute |
3. JunOS Space Configuration
3.1 Authentication Server Configuration
 |
| Authentication Server |
3.2 Define a Remote Profile 'admin'
 |
| Remote Profile - admin |
3.3 Configure JunOS Attribute in TekRadius
Basically, returned authorization data in the RADIUS server are stored as vendor-specific attributes (VSAs). Therefore, you need to update the Juniper dictionary file (Vendor Juniper in Dictionary Editor) in the RADIUS server with the Junos Space defined VSA (Juniper-Junosspace-Profiles). Users in the RADIUS server database should be assigned to return this VSAs, the values of which must correspond to the remote profiles created in the Junos Space server.
 |
| new vsa - Juniper-Junosspace-Profiles |
 |
| New Success-reply Attribute |
Assign this attribute with a value 'admin', which is matching the JunOS Space remote profile name we created at step 3.2. This value will be returned to JunOS Space to do authorization once authentication succeed.
4. Verify
You should be able to log in with your AD account name and AD password.
4.1 from TekRADIUS server
Here is log from TekRadius server.
01/09/2015 8:50:18 PM - Active Directory Authentication commencing for user 'yanjohn'
01/09/2015 8:50:18 PM - Check items control - Start (Group : admin).
01/09/2015 8:50:18 PM - Check items control - Stop (Group : admin).
01/09/2015 8:50:18 PM - Windows authentication successfull for user 'yanjohn'
01/09/2015 8:50:18 PM - Fetching Success-Reply items - Start.
01/09/2015 8:50:18 PM - Fetching Success-Reply items - Stop.
01/09/2015 8:50:18 PM - Generating Reply Packet - Start.
01/09/2015 8:50:18 PM - Generating Reply Packet - Stop.
RadAuth reply to : 10.94.200.18:59944 - 01/09/2015 8:50:18 PM
Size : 82
Identifier : 24
Attributes :
Juniper-Junosspace-Profiles = admin
cisco-avpair = shell:priv-lvl=15
Service-Type = 7
4.2 from JunOS Space Audit Logging
 |
| Audit Log |
Reference:






No comments:
Post a Comment